Cybersecurity trends in 2024
How innovation and investments in cybersecurity and AI are driving the CISO agenda and priorities for SaaS businesses.
Cybersecurity has long been in the limelight of the cloud economy, but in 2024 it is growing into one of the most promising sectors of innovation and traction across private and public markets. Today Chief Information and Security Officers (CISOs) are sought after C-Suite leaders as they play critical roles in supporting a company’s growth and maintaining trust across customers, partners, and employees. And as long-time investors in the industry, we’ve witnessed breakout names such as Wiz, the fastest growing SaaS company ever, and Axonius, one of tech’s latest Centaurs ($100M+ ARR), as role models showcasing what’s possible within the cybersecurity cohort.
Both public and private cybersecurity businesses have generally performed well within recent years, particularly in comparison to the broader tech market.
Cybersecurity’s momentum in the public market
Public cybersecurity companies have reached unprecedented market capitalizations, with notable examples including ZScaler at $26 billion, Fortinet at $49 billion, and Crowdstrike at $71 billion. For the first time, Palo Alto Networks has exceeded a market capitalization of $100 billion, marking a significant milestone in the industry.
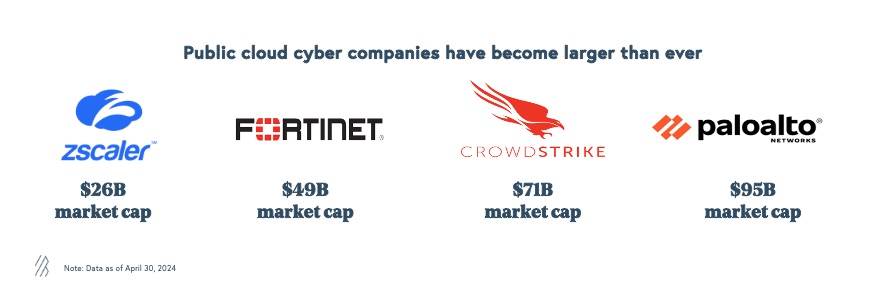
Historically, cybersecurity spending was just a fraction of total IT expenditure, resulting in smaller cyber-only companies. The continued growth in this sector is promising for entrepreneurs supporting the industry and for CISO leaders who are integral to their organizations, as they often report directly to the boards of their companies and are increasingly at the helm of the entire IT function.
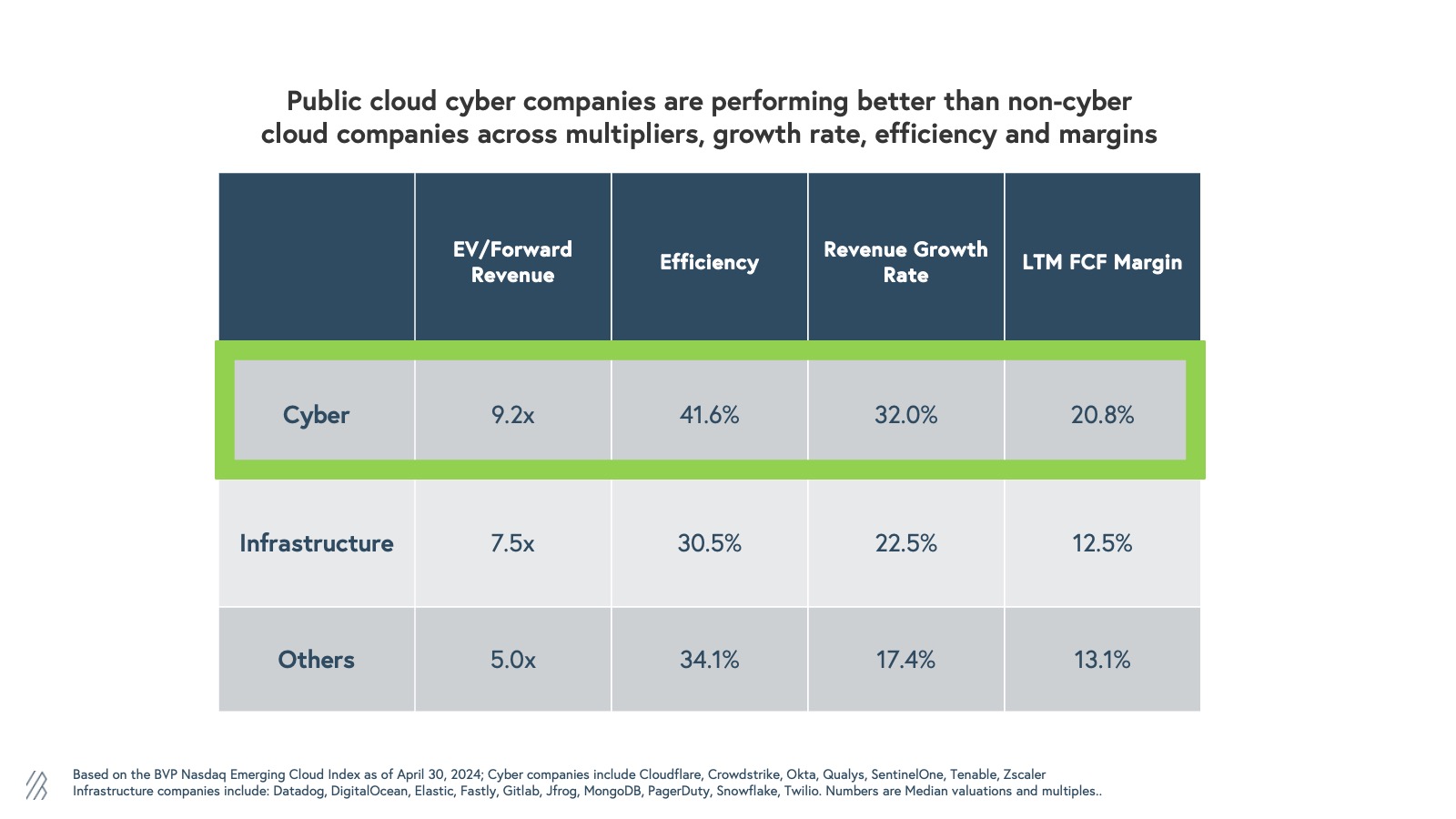
At Bessemer Venture Partners, our analysis shows that public cloud cybersecurity companies are outperforming their counterparts in the public cloud sector. Cybersecurity companies exhibit higher multiples, largely because they tend to operate more efficiently and grow at a faster pace. Additionally, the growing emphasis on security has made cybersecurity budgets more robust and resilient compared to other enterprise spending, further fueling the growth of these companies.
Cybersecurity’s traction in the private market
On the private side, we’re seeing continued promise and growth, especially among later stage cybersecurity startups. Last year, we surveyed over 400 private cloud companies across various metrics including geography, funding, hiring, and financing. Our findings revealed that the cybersecurity cloud category boasted the highest number of companies with over $300 million in cash reserves on their balance sheets.
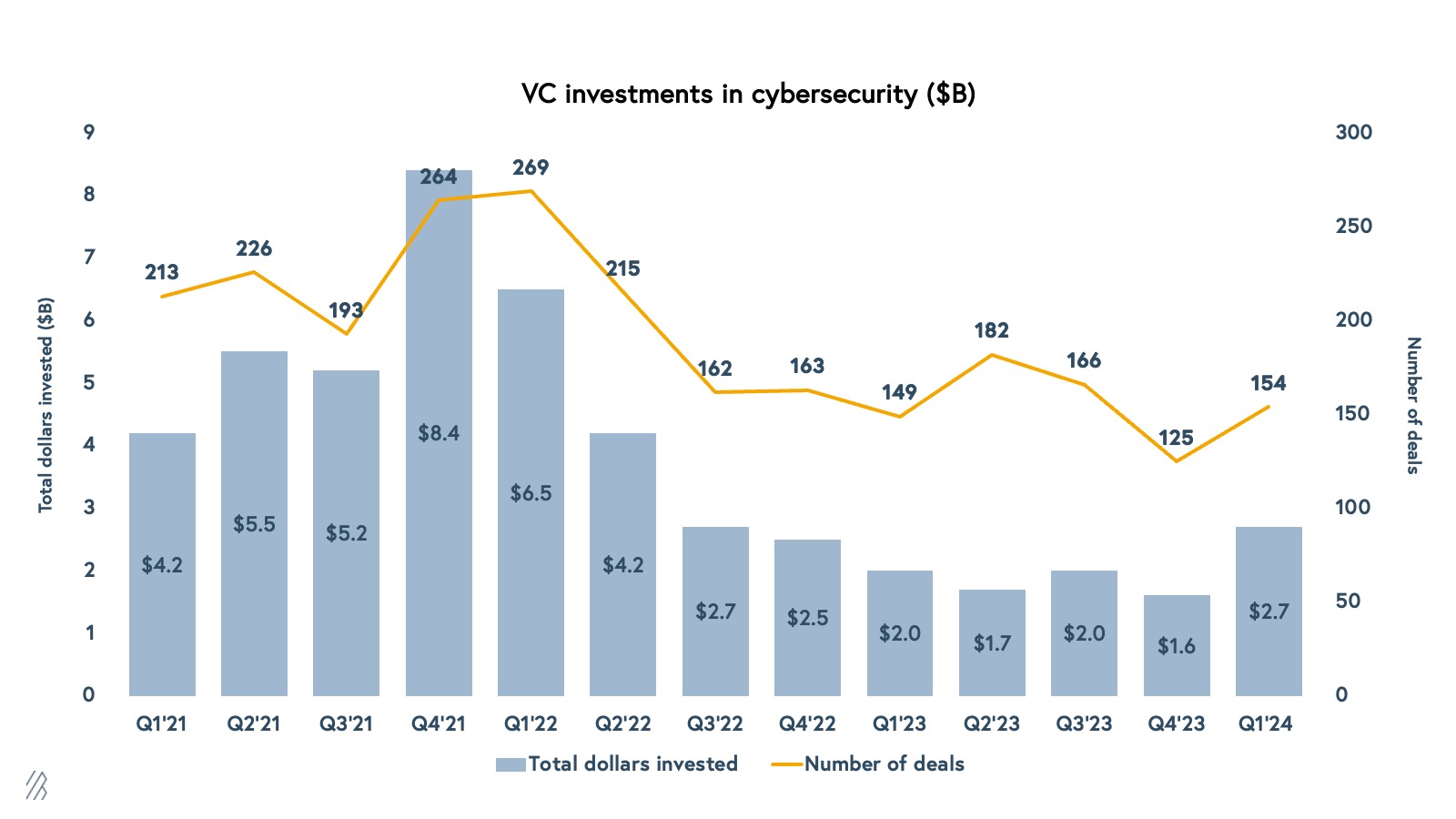
In Q1 of 2024, VC invested $2.7B into cybersecurity startups across 154 deals.
Since VC’s peak investment activity, global cybersecurity funding has dropped 58%. In 2021, over $23.3 billion was raised by cybersecurity companies. By 2023, VC saw that number drop to $7.3 billion, mirroring the broader venture capital pullback. However, after several quarters of sluggish numbers, cybersecurity startups saw a pickup in venture dollars in the first quarter of 2024 with $2.7B total dollars invested across 154 deals.
As part of the RSA season and our annual reflection at Bessemer Venture Partners, we explore the five trends impacting the CISO agenda, what’s driving entrepreneurship, and where we see investable opportunities in the cybersecurity market for 2024.
Five cybersecurity trends for 2024
Trend 1: Consolidation of the cyber market continues
We are witnessing a growing trend among major players in the cybersecurity industry, who are increasingly turning to "product-only" acquisitions to build comprehensive platforms when they cannot develop innovative alternatives in-house quickly enough. This phenomenon has always been present in the cybersecurity sector but is now occurring at an unprecedented pace, significantly impacting market structures and venture capital investment strategies.
Take Palo Alto Networks, for example. CEO Nikesh Arora expressed on LinkedIn that the future of cybersecurity hinges on integrated platforms that utilize AI for quicker and more effective security outcomes. This shift could eventually make point solutions obsolete if taken to the extreme. As budgets tighten, the appeal of point solutions diminishes, with some CISOs opting to invest in broader platform solutions that are already entrenched in their existing environment.
Reflecting on the past year's acquisitions valued over $100 million, we observe two main trends: (1) most acquired companies had between 10 and 50 customers and were primarily targeted for their teams and products, and (2) the acquisition price for “product-only” companies has increased with a median of ~$200 million to $300 million over the past year.
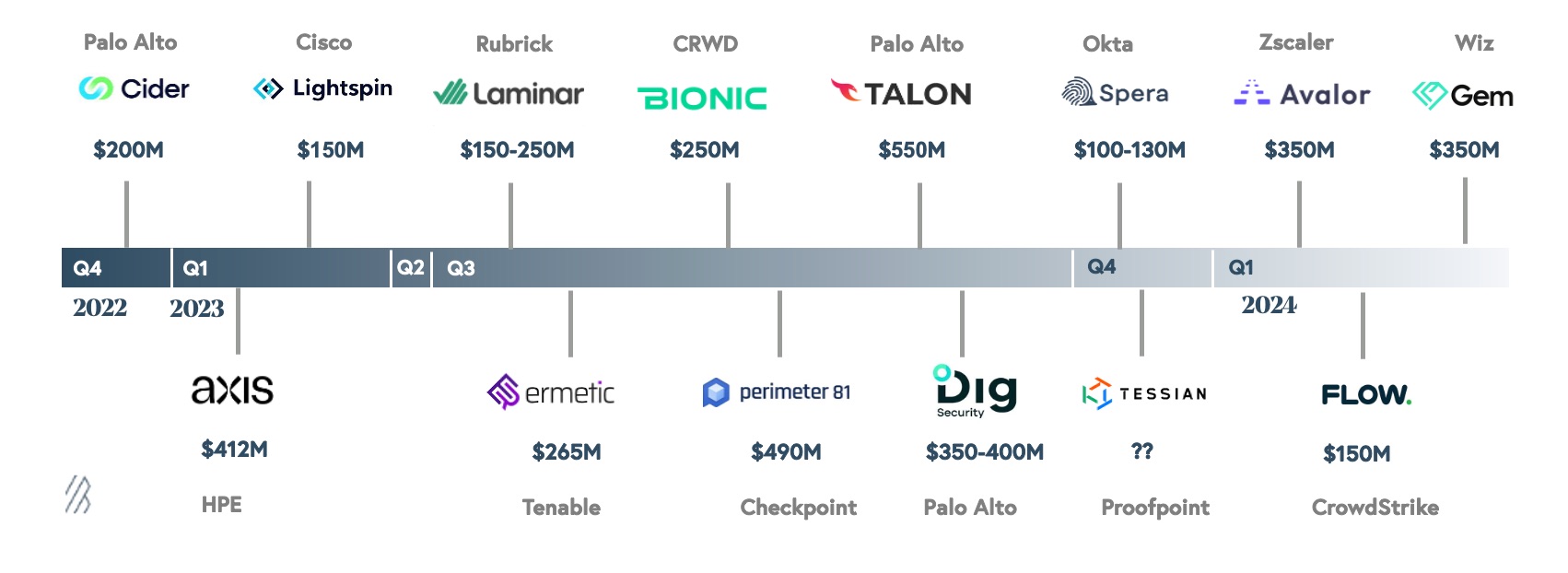
The rise of “platformization” can not be understated, however, this does not minimize a dynamic we see continuing in cybersecurity: a few vendors will never completely control cybersecurity. There will always be new areas for innovation and attack vectors which need to be protected. These factors drive entrepreneurship in cybersecurity, startup creation, and innovation to help protect businesses from new threats.
A few vendors will never completely control cybersecurity.
Although security practitioners generally favor purchasing from fewer platforms, we believe CISOs will always continue to require best-of-breed solutions to safeguard their businesses against evolving threats. “As long as bad actors keep finding new ways to attack, innovative startups will remain indispensable for businesses seeking the latest technology to stay protected,” said Cassio Goldschmidt, Chief Information Security Officer of ServiceTitan.
In addition, there remains a significant opportunity for tools that can automate, orchestrate, and enhance the efficacy of existing systems already deployed by CISOs.

Trend 2: Cybercriminals exploit AI tools for malicious attacks
AI now wields a dual-edged influence reshaping the cybersecurity landscape. This dynamic necessitates continuous innovation in defense strategies to counteract increasingly sophisticated threats.
On the attack front, AI is empowering adversaries with more complex methods such as advanced phishing schemes and deepfakes. Noteworthy incidents include a Russian deepfake of the U.S. Ambassador and a deceptive deepfake impersonating a CFO to prompt an HSBC employee to transfer $25 million. A report by cybersecurity firm SlashNext reveals a dramatic increase in these tactics: malicious phishing emails rose by 1,265%, and credential phishing surged by 967% since the fourth quarter of 2022. Cybercriminals are exploiting generative AI tools like ChatGPT to create highly targeted business email compromise (BEC) and other phishing campaigns. And we are already seeing widespread use of other AI tools like voice cloning services to deliver more impactful social engineering attacks. The rapid evolution of these AI-based threats—in speed, volume, and complexity—signals a pressing need for advanced defensive mechanisms in the cybersecurity sector.
Malicious phishing emails rose by 1,265% since the end of 2022.
Trend 3: AI counterattacks fraud and deep fakes
Conversely, AI is also bolstering cybersecurity defenses. Through automation and sophisticated AI-based security modules, these tools can detect and take the first steps in responding to threats thus helping security teams respond faster and more efficiently, enhancing cybersecurity resilience.
Our recent investments underscore our commitment to leveraging AI for defense. We have backed Clarity, a solution that secures media from deep fakes, and Torq, which has launched Socrates. This new product uses cutting-edge Large Language Models (LLMs) and AI Agents to intelligently analyze and understand organizations' SOC playbooks, becoming an integral extension of their SOC teams.
There has been an explosion of AI-related security products over the past 12 months, including both tools leveraging AI to help empower security analysts and tools to help protect employees using AI. However, when we speak to CISOs about their top priorities, tools to secure employee usage of AI rarely crack their top five. Our view is that this trend is inevitable, but we are still in the very early days of figuring out where AI will have the biggest impact on improving an organization’s security workflows and posture, and where AI usage will require bespoke tools to secure. We know that the industry is in desperate need of tools to extend security teams and automate lower-level tasks, so we are excited to continue investing in this theme. But there are still many open questions around what the right form factor is, and whether this ultimately looks more like a security copilot, an AI Agent, or a new platform entirely, such as an AI-native SIEM.
Long term, AI-powered security services will accelerate threat detection and prediction, alert aggregation, and behavioral analysis, among other capabilities. By integrating these advanced technologies, organizations can establish a more robust and proactive defense mechanism against evolving cyber threats, ensuring greater security and resilience in an increasingly digital world.
Trend 4: Growing importance of identity, and bringing the PAM, AuthN, and AuthZ solutions to the cloud
Identity, Privileged Access Management (PAM), Authentication (AuthN), and Authorization (AuthZ) are fundamental to establishing robust cybersecurity frameworks within any organization. These elements are crucial for protecting sensitive data and systems by ensuring that only legitimate users and entities have the appropriate levels of access to resources.
While the existing identity stack is well established, the entire category is being reinvented at the moment to adapt to the changing needs as enterprises move to the cloud, adopt a long tail of SaaS applications and shadow IT, and increasingly open their networks to third party and non-human identities. Security teams must navigate complex issues like adopting multi-factor authentication (MFA), managing entitlements, setting appropriate authorizations, right-sizing over-provisioned access, managing the lifecycle of resources and identities, handling the increasing number of non-human identities (such as those managed by Astrix), and addressing the sprawl of SaaS applications. Our Operating Advisor Jason Chan has outlined these challenges as well as the best practices that security leaders should aim for in his Atlas guide on the building blocks of modern enterprise identity.
The market is responding with a growing array of solutions designed to address these challenges. Some focus on optimizing workflows, others use AI to better understand usage and automate authorization decisions, and some provide a comprehensive view of an organization’s identity posture. With most companies having already established basic authentication frameworks through platforms like Okta and Microsoft Active Directory, we anticipate most of the focus going forward will be on advanced identity management tools helping to further operationalize modern identity best practices. We are already a few years into this identity technology shift, however, the industry still has a long way to go in adopting best practices, so we still think there are still many opportunities for startups to help ease the pain and streamline this transition.
Trend 5: CISOs go “back to basics”
CISOs in our community report that many are going back to basics and battening down the hatches — while the emergence and adoption of AI is being applied to traditional security areas, the CISO demand for AI-driven solutions has not caught up yet with the growing number of companies in this space. The reality is that most of the day-to-day items on a security team’s agenda go back to basic blocking-and-tackling initiatives.
For example, we have heard CISOs prioritizing their security hygiene, including everything from improving the patching practices, and refactoring old code with known vulnerabilities, to doubling down on securing identity. As Geoff Belknap, the CISO of LinkedIn told us, “AI-enabled threats have just raised the bar for all of us in needing to increase our security hygiene — there is no silver bullet.”
“AI-enabled threats have just raised the bar for all of us in needing to increase our security hygiene — there is no silver bullet.”
In addition, CISOs now face a much greater compliance challenge with the SEC’s latest regulations requiring greater disclosure and reporting from CISOs regarding security incidents and risk management. This is clearly taking up an increasing amount of bandwidth from security leaders and we expect this will lead to opportunities for more products focused on compliance, third-party risk management, and governance.
There is no rest for the CISO — especially as the “threat landscape” evolves each day with fraud taking on new disguises and Ransomware-as-a-Service (RaaS) remaining a prominent concern. Given this reality, we expect vendor security demands to grow and solutions to continue to address basic cybersecurity hygiene, education, awareness, and regulation.

The cybersecurity horizon
Today, the role of a CISO has never been more challenging. Yet, this is not just a business issue—it's a global concern that affects every country. At the Davos meeting in January, world leaders discussed how cyber insecurity represents a significant and ongoing risk across various time horizons, encompassing threats from malware and deep fakes to misinformation.
As the threat landscape grows more complex, technological solutions are becoming increasingly sophisticated. At Bessemer, we are confident that cybersecurity leaders will not only discover new strategic and technological solutions to protect their businesses but that a new wave of entrepreneurs will also emerge. These innovators are poised to develop the next generation of cybersecurity solutions, addressing the critical needs of global enterprises and government entities alike.







